Medical care is a billion buck market. Last years is rather apparent that a lot of person details has actually been jeopardized. This has actually straight affected the integrity of health and wellness applications and the market concerned.
For that reason, to deal with restraints of Personal Privacy, Protection, Enforcement and Violation Notice, the Medical Insurance Transportability and Liability Act also known as HIPAA has actually laid guidelines.
What is HIPAA Conformity?
HIPAA conformity includes meeting the needs of the Medical insurance Transportability and Liability Act (HIPPA) of 1996, its succeeding modifications, and any type of associated regulation such as the Wellness Infotech for Economic and Medical Wellness (HITECH) Act.
What does it suggest to be in conformity with HIPAA?
HIPAA establishes the requirement for delicate person information security. Firms that take care of safeguarded health and wellness details (PHI) should have the physical, network, and procedure safety procedures in position and follow them to make certain HIPAA Conformity.
The USA mandate their addition to ensure that clients have accessibility to an extra sensible application.

Situation: Anthem, the leading United States Insurance coverage company needed to pay a hefty rate
Burglary of person information can bring about hefty losses, scams, blackmail and whatnot. United States regulation mandates HIPAA in order to keep the personal privacy of such vital details. And the situation that complies with is an appropriate exemplification of what makes HIPAA crucial in applications–
Anthem is the biggest United States Insurance coverage company. It provides its substantial health and wellness advantages and treatment to United States people under their associated health and wellness plans. The firm has actually experienced the biggest violation in United States health care.
Cyber enemies targeted the firm’s innovative IT systems creating an ePHI (digital Person Health and wellness Details) violation of virtually 79 million individuals in a collection of cyber assaults. Jeopardized details consisted of SSN, addresses, names, work details, e-mail addresses, day of birth and clinical recognition number.
This innovative consistent risk strike had the single objective of removing the details of individuals consequently breaking civil liberties. Anthem had actually stopped working to fulfill the HIPAA standards which led to a lawful commitment on the firm from the customer for no much less than $115 M. In addition, the firm needed to invest virtually $260 M to relieve safety procedures.
Any kind of company, huge or little, might deal with significant effects if they disregard HIPAA guidelines unless they have the ability to manage an insane quantity of cash and concession on their individuals’ depend on.
HIPAA to assist health care Suppliers and People
Anthem might have conveniently stayed clear of the scenario by mindful analysis of safety systems and procedures.
The regulation needs doctor such as healthcare facilities and Company Associates (3 rd events taking care of individuals’ details) to meet the pre-requisites of HIPAA. The regulation additionally needs conformity also when the celebration has an indirect connection with PHI.
The conformity requires normal analysis and audits for the safety and personal privacy of health care details. The analysis includes Physical and Technical safeguards that HIPAA describes.
- Technical safeguards– These make certain emergency situation gain access to, file encryption, login, previous tasks, and so on
- Physical safeguards– Shielding the system consisting of PHI such as Computers, information centres, web servers, laptop computers, and so on
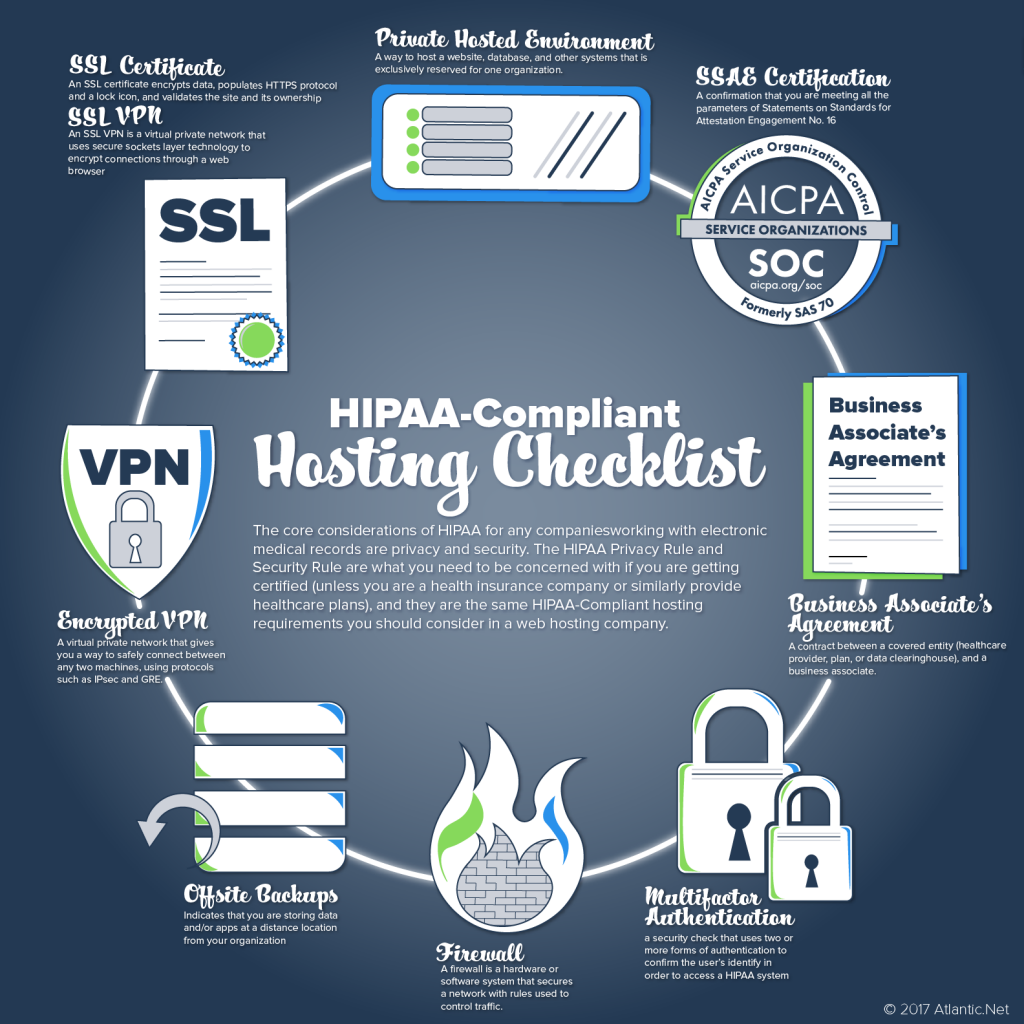
And a Includes List to validate your Hippa Compliant Medical care application
| Attributes | Information |
| Secure Transmission | People’ information shared over a network requires miraculous safety. |
| Accessibility Control | This attribute mandates accrediting accessibility to PHI. HIPAA mentions no individual needs to have accessibility to details they are not permitted to. Also the individuals can reach choose that need to or need to not have accessibility to his/her PHI. |
| Validating entity | Every customer attempting to access to People’ information need to offer his/her recognition. It is feasible with the execution of Password, Biometrics, physical recognition, and PIN (Individual Recognition Number). |
| Back-up | To keep the stability consider person’s information, it is essential to maintain PHI in duplicates. |
| Display the task on PHI | PHI is susceptible to make use of by employees of all degrees. It is essential to check any type of solutions, alterations, removals or accessibility to the information that is at risk to strike. |
| Disposing of Securely | Doctor or Company Associates need to specify clear approaches for effective disposal of PHI when it is no more needed. Along with PHI, healthcare companies need to additionally damage the resource of PHI such as pen drives or floppies. |
| Secure the information | Among the tested methods to make certain PHI safety is to secure it prior to transmission to ensure that the recipient can just decrypt it with a trick. |
| Task Logs and Audit Controls | The audit regulates needed under the technological safeguards exist to sign up attempted accessibility to ePHI and document what is performed with that information once it has actually been accessed. |
| Wheelchair of Instruments | Security of mobile phones is critical as they are conveniently shed or mistreated. Actions such as securing, securing, or from another location erasing the information require motivation amongst doctor. |
Allow Wildnet Technologies create a HIPAA certified Medical Care Application for you
Wildnet’s group of Specialist Internet, Mobile Applications and Salesforce Cloud CRM Developers have riches of experience in creating best-in-class health care applications Undoubtedly, these applications meet only pre-requisite– HIPAA conformity.
As the regulation of the USA mandates HIPAA for PHI safety and stability, it is essential for all Software application Developers to successfully fulfill HIPAA standards. Which is specifically what we do! We make health care applications keeping in mind the value of end-user information.
Do you have an application in mind? Contact us!